
And although this may sound like a plot from a science fiction film, it is a growing concern among researchers who have demanded officials implement a privacy and security framework to block hackers from reading our neural signals.
Brain-computer Interfaces (BCIs) are widely used in the medical field and other industries, including marketing, gaming and entertainment. Although this technology was initially created to improve and enhance the quality of human lives, in the wrong hands it will wreak havoc on them.
Researchers at the University of Washington say that time is running out and officials need to employ a privacy and security framework to stop those who would use our own brains against us, reports Motherboard.
'There's actually very little time,' electrical engineer Howard Chizeck told Victoria Turk with Motherboard over Skype.
'If we don't address this quickly, it'll be too late.'
Chizeck and fellow engineer Tamara Bonaci are conducting hacking research that includes the use of BCIs, combined with subliminal messages inserted into video games to gather users' private information.
For example, when playing a video game users may see logos of familiar brands pop-up on the screen that just vanish. It wasn't your eyes playing tricks on you, hackers put those images in the game and they were recording your 'brain's unintentional response to them' using a BCI, which can be a wearable that monitors stress levels or a cap covered in electrodes.
And hackers won't just stop at narrowing down your favorite retailer.
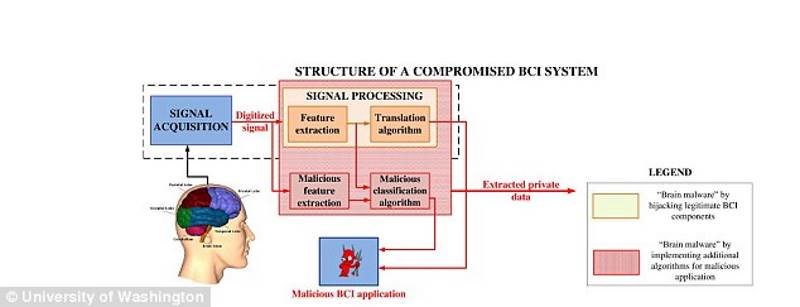
How can cyberthieves hack our brains
Experts at the University of Washington reveal hackers are inserting images into dodgy apps and recording our brain's unintentional reaction using brain-computer interfaces.For example, when playing a video game users may see logos of familiar brands pop-up on the screen that just vanish.
Hackers put those images in the game and they were recording your 'brain's unintentional response to them' using a BCI, which can be a wearable that monitors stress levels or a cap covered in electrodes.
This technology could one day be used by advertisers to gather more information about their customers.Also, police officers and government officials could use this method to convict criminals or as a 'remote lie detector test'.
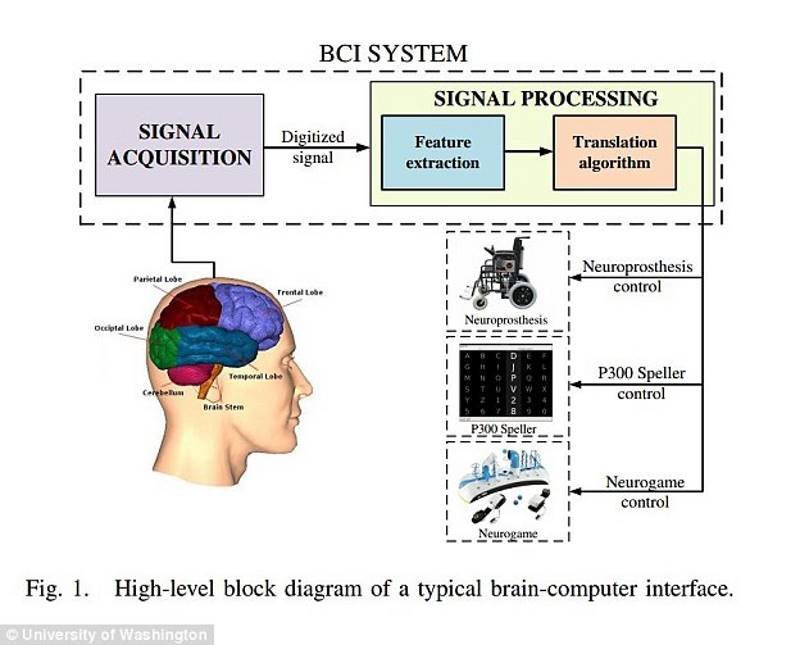
What are brain-computer interfaces?
Brain-computer interfaces (BCIs) are communication systems that link the brain to the outside world, which includes fitness bands, game controllers, a cap fitted with electrodes, among others.
When using this technology, a person's 'message' does not take the same normal path of peripheral nerves and muscle, but are encoded in electrophysiological signals - such as electroencephalograms (EEG).
The technology was initial developed to assist with the growing disabled population.
The first BCI was developed in the 1970s, but has since been developed for assistance, augmentation and repair of cognitive and sensorimotor capabilities of people with severe neuromuscular disorders, such as spinal cord injuries or amyotrophic lateral sclerosis. But most recently, BCIs have found their way into fiction, gaming, entertainment and marketing.
There are currently several consumer-grade BCI-based systems: Emotive System, NeuroSky and gtec Medical Engineering.
The supported applications can broadly be classified into: accessibility tools, such as mind-controlled mouse and keyboard, hands-free arcade games, such as Brain Bats, mind-controlled Pong game and "serious games", games with purpose other than pure entertainment, such as attention and memory training. (University of Washington )
These cyberthieves can find out what political party you affiliate with, religious beliefs or sexual orientation - things that could one day be used to damage your reputation.
'Broadly speaking, the problem with brain-computer interfaces is that, with most of the devices these days, when you're picking up electric signals to control an application... the application is not only getting access to the useful piece of EEG needed to control that app; it's also getting access to the whole EEG,' explained Bonaci.
'And that whole EEG signal contains rich information about us as persons.'
Chizeck also explained that it isn't the invisible hackers that reap the benefits of this technology, police officers and government agencies could also gather information about someone in order to convict them or use as a 'remote lie detector', he said.

'It's been known in neuroscience for a while now that if a person has a strong emotional response to one of the presented stimuli, then on average 300 milliseconds after they saw a stimulus there is going to be a positive peak hidden within their EEG signal,' she said.
Although it is still impossible to tell what someone's exact emotional response is to an image, it is possible to strategically place different images on the screen and narrow it down that way, explains Bonaci - this method has proved to be 72% to 84% accurate.
And hackers can track an individual over time, which allows them to get an even clearer picture about the person.
BCIs have long been part of the gaming scene - from the hand-held controller to the modern addition of technology that monitors your vitals, like fitness trackers.
Chizeck and Bonaci are not just working on understanding this method of gathering information, but are also investigating how it plays into privacy and security.
'While federal law protects medical information and generally guards against unfair or deceptive practices, few rules or standards currently limit access to BCI-generated data,' the team wrote in the 2014 paper 'App Stores for the Brain: Privacy & Security in Brain-Computer Interfaces'.
'Existing and emerging privacy and security threats may be viewed as an attack on human rights to privacy and dignity'.
Researchers use game control to hack peoples brains
Researchers from the University of California, University of Oxford and University of Geneva figured out a way to pluck sensitive information from a person's head, such as PIN numbers and bank information.
They used a freely available games controller costing just £190 ($299).
The scientists took an off-the-shelf Emotiv brain-computer interface, a device that costs around $299, which allows users to interact with their computers by thought, and is often used to control games.

The P300 signal is used by the brain when a person recognizes something meaningful, such as someone or something they interact with on a regular basis.
It is released by the brain around 300 milliseconds after recognition occurs, hence its name.
The team used a picture of President Barack Obama to test the readings, and saw a spike of recognition from participants.
They were also shown their home, which caused a similar reaction.
'These devices have access to your raw EEG [electroencephalography, or electrical brain signal] data, and that contains certain neurological phenomena triggered by subconscious activities," says Ivan Martinovic, a member of the faculty in the department of computer science at Oxford.
'So the central question we were asking with this is work was, is this is a privacy threat?'
The team found they could find a person's home 60% of the time with a one in ten chance, and had a 40% chance of recognising the first number of a PIN number. In the paper that the scientists released, they state that 'the P300 can be used as a discriminative feature in detecting whether or not the relevant information is stored in the subject's memory.
'P300 has a promising use within interrogation protocols that enable detection of potential criminal details held by the suspect,' the researchers said.The duo argues that a method that prevents and moderates BCI enabled privacy and security issues 'must be developed now'.
_____
Chizeck and Bonaci have proposed their own idea to combat this issue, which would 'filter' signals so apps would only have access to the specific data they require.
In the 2014 paper, they deemed the method 'BCI Anonymizer', which would pre-process the signals before they can ever be stored and transmitted - removing all the user's private information.
'Unintended information leakage is prevented by never transmitting and never storing raw neural signals and any signal components that are not explicitly needed for the purpose of BCI communication and control,' reads the paper.



Reader Comments
to our Newsletter