The malware was found on machines in the United States, Brazil and India by researchers at Morphus Labs. It was discovered on computers owned by an energy company in Brazil with subsidiaries in the U.S. and India. Renato Marinho, one of the researchers who uncovered Mamba, detailed the ransomware in an article on LinkedIn.
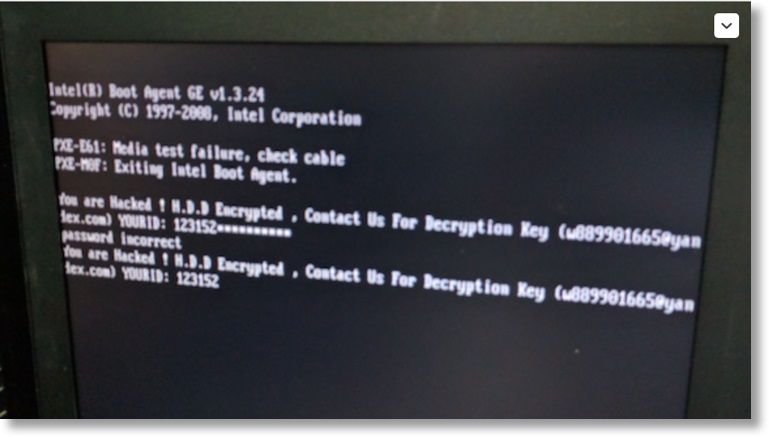
Most ransomware utilities encrypt the files in your personal folders but leave the computer's operating system intact. A popup window is then displayed to allow you to purchase a decryption key and retrieve your data. Mamba goes a few steps further. It prevents your computer from starting up, displaying a custom prompt for a decryption key before loading your machine's OS.
Mamba achieves this by overwriting your computer's master boot record (MBR). The MBR essentially stores a list of all your installed operating systems. When you turn your computer on, the default OS stored in the MBR is started up. By inserting itself into the MBR, Mamba can display a custom prompt to the user before the usual operating system starts.
Mamba is an advanced form of ransomware and utilises full-disk encryption. This encrypts every file on the hard drive, instead of just the important data created by the user.
Until the correct decryption key is supplied, the target machine cannot load any other operating system. In the enterprise and server environments Mamba appears to be targeting, the attack could be very serious.
"Mamba encrypts the whole partitions of the disk," Marinho said to Threatpost. "It uses a disk-level cryptography and not a traditional strategy of other ransomware that encrypts individual files."
Mamba is sophisticated but it does contain a few flaws. According to Marinho, Mamba appears to use the same password for all its victims, potentially making it easier to bypass. The password may be linked to something tied to the victims' environment, such as their hostname, but that data is relatively easy to obtain.
The malware's creators are charging 1 bitcoin each for decryption keys. So far, the bitcoin wallet being used to run the campaign has received 4 coins. That suggests that four victims have already paid up, although the wallet could also be used for other transactions. Morphus Labs could not determine the identity of the attackers.
Mamba is currently limited to Windows-based machines so Linux users are safe from this attack. It is believed the infection arrives on target machines through downloads from malicious websites. As ever, staying vigilant while browsing the web and opening suspicious emails will help to lower the risk of attack.




Reader Comments
to our Newsletter