The top-secret PRISM program allows the U.S. intelligence community to gain access from nine Internet companies to a wide range of digital information, including e-mails and stored data, on foreign targets operating outside the United States. The program is court-approved but does not require individual warrants. Instead, it operates under a broader authorization from federal judges who oversee the use of the Foreign Intelligence Surveillance Act (FISA). Some documents describing the program were first released by The Washington Post on June 6. The newly released documents below give additional details about how the program operates, including the levels of review and supervisory control at the NSA and FBI. The documents also show how the program interacts with the Internet companies.
These slides, annotated by The Post, represent a selection from the overall document, and certain portions are redacted.
Read related article.
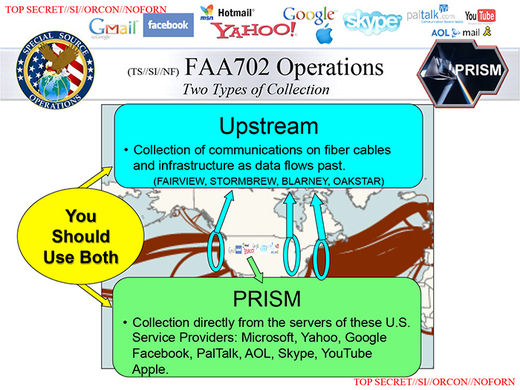
New slide published July 10Upstream programThis slide shows PRISM as only one part of the NSA's system for electronic eavesdropping. The "Upstream" program collects from the fiber-optic cable networks that carry much of the world's Internet and phone data. The underlying map depicts the undersea cables that connect North America to the rest of the world.
Slides published June 29
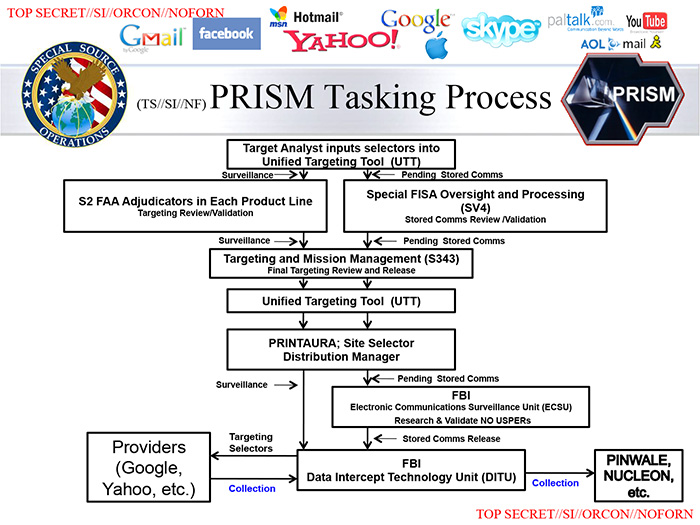
Acquiring data from a new targetThis slide describes what happens when an NSA analyst "tasks" the PRISM system for information about a new surveillance target. The request to add a new target is passed automatically to a supervisor who reviews the "selectors," or search terms. The supervisor must endorse the analyst's "reasonable belief," defined as 51 percent confidence, that the specified target is a foreign national who is overseas at the time of collection.
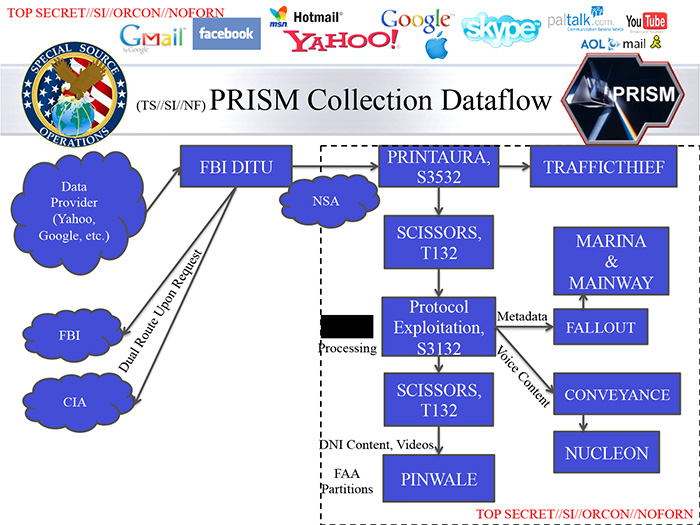
Analyzing information collected from private companiesAfter communications information is acquired, the data are processed and analyzed by specialized systems that handle voice, text, video and "digital network information" that includes the locations and unique device signatures of targets.
Each target is assigned a case notationThe PRISM case notation format reflects the availability, confirmed by The Post's reporting, of real-time surveillance as well as stored content.
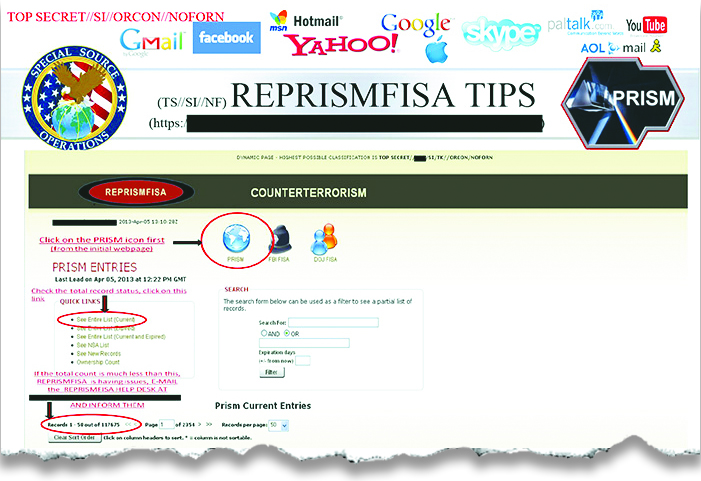
Searching the PRISM databaseOn April 5, according to this slide, there were 117,675 active surveillance targets in PRISM's counterterrorism database. The slide does not show how many other Internet users, and among them how many Americans, have their communications collected "incidentally" during surveillance of those targets.
Original slides published June 6
Introducing the programA slide briefing analysts at the National Security Agency about the program touts its effectiveness and features the logos of the companies involved.
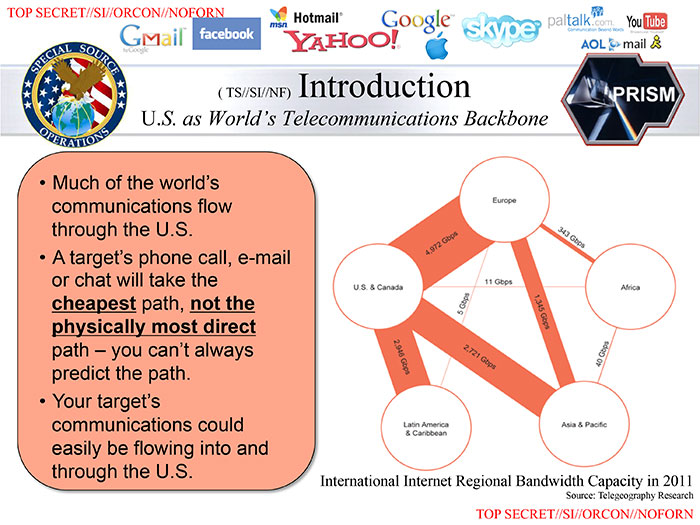
Monitoring a target's communicationThis diagram shows how the bulk of the world's electronic communications move through companies based in the United States.
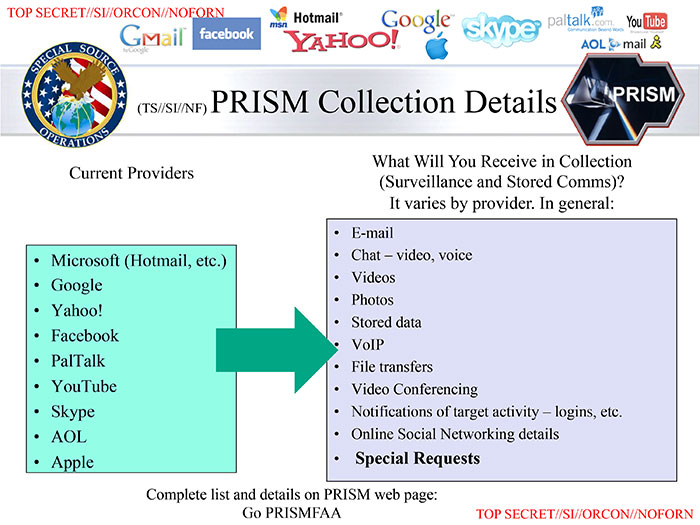
Providers and dataThe PRISM program collects a wide range of data from the nine companies, although the details vary by provider.
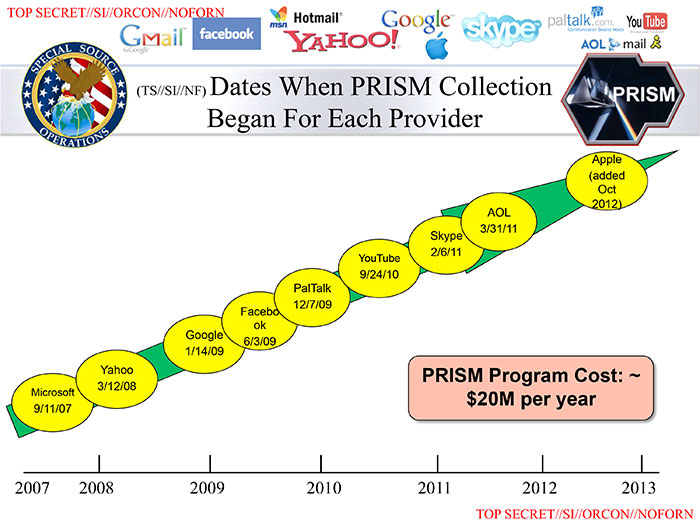
Participating providersThis slide shows when each company joined the program, with Microsoft being the first, on Sept. 11, 2007, and Apple the most recent, in October 2012.



Well, that's certainly a heckuva lot more than the associated companies damage control statements have suggested...