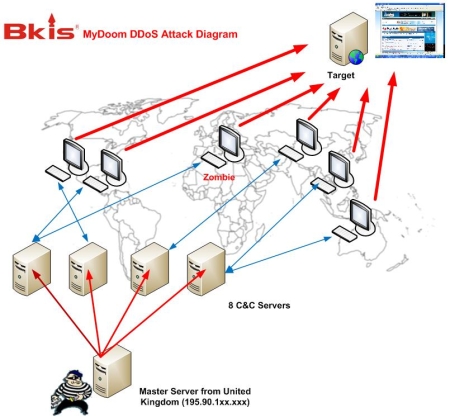
We have analyzed the malware pattern that we received from KrCERT and have located the botnet controlled by 8 Command and Control (C&C) servers via controlling code embedded in a file named "flash.gif". Every 3 minutes, zombies randomly select one of the 8 servers to connect to and to receive orders. Especially, we found a master server located in UK which controls all of the 8 C&C servers to make a series of cyber-attack last week. So the source of the attacks has been identified to be in UK. The existence of master server has never been reported before.
In order to locate the source of the attacks, we have fought against C&C servers and have gained control of 2 in 8 of them. After analyzing the logs of these 2 servers, we discovered the IP address of the master server, which is 195.90.118.xxx. This IP is located in UK. The master server is running on Windows 2003 Server Operating System..
During the past few days, the number of zombies has been estimated to be 50,000 by Symantec and about 20,000 by Government of South Korea. But, by taking control of two C&C servers and analyzing logs on these servers, we count the exact number of zombies that have been querying C&C servers to receive commands. Accordingly, there have been 166,908 zombies from 74 countries around the world that have been used for the attacks.
| No. | Country |
|---|---|
| 1 | Korea, Republic of |
| 3 | United States |
| 4 | China |
| 5 | Canada |
| 6 | Australia |
| 7 | Philippines |
| 8 | New Zealand |
| 9 | United Kingdom |
| 10 | Vietnam |
Having located the attacking source in UK, we believed that it is completely possible to find out the hacker. This of course depends on the US and South Korean governments. We have sent KrCERT and US-CERT the IP address of the attacking source.
Bkis has sent the detail of research and the information of the master server in UK to US-CERT and KrCERT.
At present, US-CERT and KrCERT are cooperating to investigate the attack source.
The Korea Communications Commission (KCC) also confirmed of the Bkis report. "The Korea Communications Commission (KCC), the country's broadcasting and telecommunications regulator, backed Bkis report and said law enforcement authorities are currently seeking cooperation with the British government to investigate the attack source".
Nguyen Minh Duc is the Senior Security Researcher / Bkis Security Director
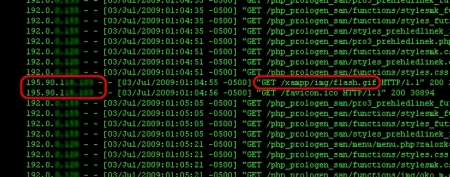



Doing some 'reader research' I see that...
A company called Global Digital Broadcast, Inc. leases the IP block from OHTelecom.
The GDB guys seem pretty sophisticated, running the what they state as being the largest Global IPTV network. TV pumped throught the Internet. Where as old television was uni-directional in the interaction, IPTV can be "interactive" in that servers can record all of our actions, where we go, whay we type and so thus, what we are thinking.
If you look at the GDB homepage, hooking up with CNN and all the major American networks, it looks like perhaps a USDoD link is there too. What is the hardest to believe though, is that such a high-end content delivery network wouldn't know that unauthorized servers were operating inside of it's network?
And one's that are controlling a massive botnet fabric. The economy sucks and everyone is looking for ways to pay for investments in technology, it may be the case here. Develop a large global network, have your own private pipe, failover (the run BGP on everything it seems) and the smarts to run it all 100% 24/7/365 well that requires alot of money. The only money that really seems to be out there in quantity is DoD projects, they are the ones driving alot of the tech related economy currently. Social networking web programming is a hot item right now.