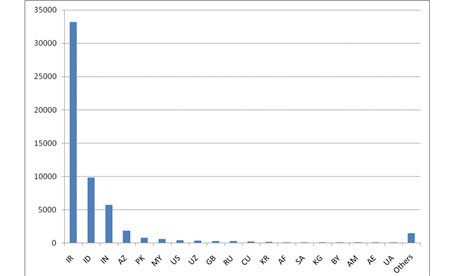
© SymantecGraph shows concentration of Stuxnet-infected computers in Iran as of August.
A computer worm which targets industrial and factory systems is almost certainly the work of a national government agency, security experts told the
Guardian - but warn that it will be near-impossible to identify the culprit.
The "Stuxnet" computer worm, which has been described as one of the "most refined pieces of malware ever discovered", has been most active in Iran, says the security company Symantec - leading some experts to conjecture that the likely target of the virus is the controversial Bushehr nuclear power plant, and that it was created by Israeli hackers.
Speaking to the
Guardian, security experts confirmed that Stuxnet is a targeted attack on industrial locations in specific countries, the sophistication of which takes it above and beyond previous attacks of a similar nature.
Latest figures, from August, show 60% of computers infected by Stuxnet are located in Iran - dramatically up from July, when it accounted for less than 25% of infections, research by Symantec shows, with the graph above (from 4 August) showing the prevalence in other countries by comparison. The company estimates that the group building Stuxnet would have been well-funded, comprising between five and 10 people, and that it would have taken six months to prepare.
Alan Bentley, senior international vice president at security firm Lumension, said Stuxnet is "the most refined piece of malware ever discovered", and that the worm was significant because "mischief or financial reward wasn't its purpose, it was aimed right at the heart of a critical infrastructure".
However Graham Cluley, senior consultant with the online security company Sophos, warned against jumping to conclusions about the target of the attack, saying "sensationalist" headlines were "a worry". Clulely is wary of reports linking Stuxnet with Israel: "It's very hard to prove 100% who created a piece of malware, unless you are able to gather evidence from the computer they created it on - or if someone admits it, of course."
But he said that its characteristics did not suggest a lone group. "I think we need to be careful about pointing fingers without proof, and I think it's more appropriate - if true - to call this a state-sponsored cyber attack rather than cyber terrorism."
Stuxnet works by exploiting previously unknown security holes in Microsoft's Windows operating system. It then seeks out a component called Simatic WinCC, manufactured by Siemens, which controls critical factory operations. The malware even uses a stolen cryptographic key belonging to the Taiwanese semiconductor manufacturer RealTek to validate itself in high-security factory systems.
The worm then takes over the computer running the factory process - which for WinCC would be "mission-critical" systems which have to keep functioning under any circumstance - and "blocks" it for up to a tenth of a second. For high-speed systems, such as the centrifuges used for nuclear fuel processing being done by Iran, that could be disastrous, experts suggested.
US army forces are aware of the threat posed by Stuxnet, general Keith Alexander confirmed this week, saying early indications showed that the worm was "very sophisticated".
Clulely told that
Guardian that Siemens has "astonishingly" advised power plants and manufacturing facilities not to change the default password that allows access to functions, despite it being exploited by Stuxnet and being "public knowledge on the web for years".
Alan Bentley, SVP International at Lumension, told the
Guardian: "There is a lot of circumstantial evidence to suggest that Iran was the target of Stuxnet. We know that the worm was designed with a specific target in mind - its makeup and the way it executes render the tell-tale signs.
"Combine this with the fact that the worm was identified by a Belarusian security firm working for an Iranian client and the fact that the nuclear power plant was not working properly for months, it is understandable that speculation points towards Iran as the target. But, without being inside the walls of the Bushehr nuclear power plant, we can't be certain."
Rik Ferguson, senior security adviser at Trend Micro, said: "Initially, it looks like a targeted attack. It saw a high percentage of infections concentrated in the Middle East. Iran being one. There's every possiblity that the [other countries affected] may have been collateral damage."
Asked whether a nation state was behind the attack, Ferguson said: "The truth is we don't know. But we can look at the concentration [of the attacks]. I don't think we can call this cyberwarfare, I would call it modern espionage. Countries have been spying on their neighbours for years - as the technology has improved, espionage has always improved, and this is step in that direction.
"It's significant because it's not just the malware but the vulnerability to infect machines - if this had been in more traditional, criminal hands it could have been more widely used, like Conficker was. This was a powerful vulnerability it exploited and usually either you sell it for a lot of money or use it for mass criminality."
David Emm, a senior security researcher at Kaspersky Lab, told the
Guardian: "We think that Stuxnet's sophistication, purpose and the intelligence behind it suggest the involvement of a state.
"This is a very sophisticated attack - the first of its kind - and has clearly been developed by a highly skilled group of people intent on gaining access to SCADA [supervisory control and data acquisition] systems - industrial control systems for monitoring and managing industrial infrastructure or facility-based processes. In contrast to the bulk of indiscriminate cybercrime threats on the internet, this has been aimed at very specific targets. It's different also because there's no obvious financial motivation behind the attack - rather the aim seems to be to sabotage systems."
However, John Pescatore, vice president for internet security at Gartner, said it was "definitely not the case" that Stuxnet would have required state sponsorship. "We've seen similarly targeted software going after credit card readers for financial gain in the past," he said. "Governments have no monopoly on the talent. We've seen attacks that looked like they were state-sponsored in the past launched by hackers for attention or citizens' groups. You cannot tell just by looking at where it landed."
The experts agree that Stuxnet marks a shift away from malware deployed for financial gain to controlling critical machinery. We are now moving into a "third age" of cyber crime, Clulely said, where the intention of making money from technical exploits is replaced by an intention to bring down critical infrastructure. "We're entering this third age as well, where there are political, economic and military ways in which the internet can be exploited - and malware can be used - to gain advantage by foreign states.
"I think we will see more and more attacks which will be blamed on state-sponsored cyber attacks. There have been numerous attacks in the past which could be said to have possible military, political or economic motives, but it is very difficult to prove that a hack was ordered by Mossad or instead dreamt up by a Macclesfield student."
Reader Comments
to our Newsletter